Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
School of Technology, Assam Don Bosco University (tinyurl.com/eee-adbu)
It’s About Time. Engineers, Happy New Year!
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
3 Bad Conditions That Cause False Differential Current In Power Transformer
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
10 Common Questions You Can Expect In Electrical Engineering Examination Test
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
This Is Why HVDC Transmission System Beats HVAC In These Essential Applications
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
A Good Grounding Of The Power Substation And Switching Station – What Does It Really Mean?
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
Analyzing Power System And Equipment Performance Through Oscillographic Records
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
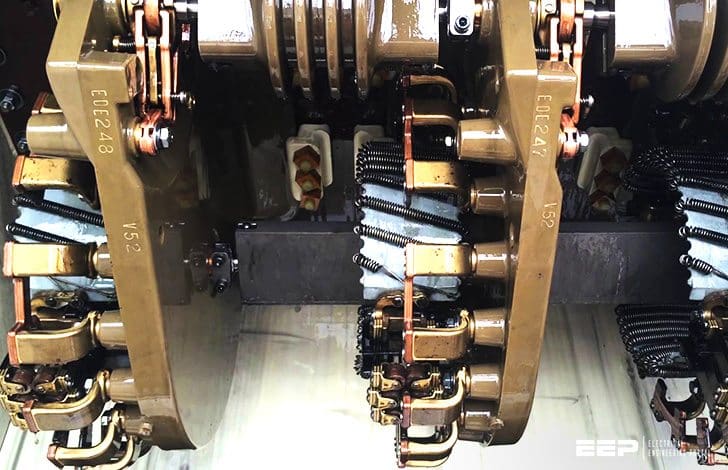
Contactor As An Important Part Of The Motor Control Gear
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
What is WiMAX? Difference between Broadband WiMax and WiFi
What is WiMAX GSM Broadband and WiFi
Introduction to WiMAX Broadband
WiMAX stands for Worldwide Interoperability for Microwave Access, a standard based wireless communication technology to provide high speed, long distance broadband connectivity for domestic and business purposes. It works on the principle of Orthogonal Frequency Division Modulation technique. It is a 4th generation wireless mobile access technology.
Also Read: What is ZigBee Technology and How it works?
Operating principle of WiMAX is same as that of Wi-Fi. A computer or a laptop, which is equipped with WiMAX, would receive data from the transmitting station, using encrypted data keys.
WiMAX system consists of a WiMAX tower and a WiMAX receiver. A WiMAX tower can provide coverage to a large area, whereas a WiMAX receiver can be a laptop or a Personal Computer Memory Card International Association (PCMCIA) card.
The tower station can be connected directly to internet using high bandwidth, wired connection or to another tower station using Line of Sight, Microwave link.
WiMAX connection is accessible to residential areas through interface options like RJ-4 Ethernet connection and RJ-11 telephone connection. For business applications, interface options include T1/E1 interface with a 10/100 BT Ethernet connection.
So as per definition, WiMax seems to be like Wifi, so where lies the difference? Here in this article, Let us discuss about few points which makes WiMAX different to Wi-Fi.
Also Read: An Overview of RFID Based Library Management System
IEEE Standards of WiMAX & Wifi
While Wifi is based on IEEE 802.11 standard, WiMAX is based on IEEE 802.16 standard. IEEE 802.11 standard (Wireless Local Area Network (LAN) working group) is used to provide Wireless Local Area Network (WLAN) standards for short distance wireless networks. Popular versions are IEEE 802.11b, 802.11g and 802.11n.
IEEE 802.16 standard (Broadband Wireless Access Working Group) is like IEEE 802.11 standard in architecture, difference being in its application to provide standards for Broadband Wireless Metropolitan Area Networks (WMAN). It employs medium access control (mac) as well as physical layer specifications, allowing multiple physical layers. Popular versions are 802.16a, 802.16d and 802.16e.
Range
WiMAX provides both line of sight as well as non-line of sight connectivity. For line of sight connectivity, with the help of strong antennas, coverage area of up to 9300 square kilometers (sq-kms) is possible. Non-line of sight connectivity is like Wi-Fi connection. WiMAX covers a radius of 50 kilometers (km).
On the other hand, Wi-Fi is a short distance wireless means of connectivity up to 30 meters for indoor applications and up to 100 meters for outdoor coverage. Unlike WiMAX, Wi-Fi provides only line of sight connectivity.
Operating Frequency Band
WiMAX technology provides two types of wireless services – Line of sight service with operating frequency band up to 66 GHz, whereas for non-line of sight service, the operating frequency is between 2 to 11 GHz.
The higher frequency range was set by the original 802.16a standard, whereas the lower frequency range was set later by the 802.16d standard, allowing less attenuation and improved performance. While 2.5 to 3.5 GHz frequency band is licensed, the 5.8 GHz frequency spectrum is unlicensed.
On the contrary, Wi-Fi operates in the unlicensed 2.4 GHz and 5 GHz bands.
Channel Bandwidth
WiMAX networks have flexible channel bandwidth range from 1.25 MHz to 20 MHz, whereas Wi-Fi networks have fixed channel bandwidth of 20 MHz.
Aslo Read: What are Industrial Communication Networks? An Overview
Communication Type
WiMAX supports full duplex communication with 256 FFT OFDM (Orthogonal Frequency Division Modulation) along with single carrier and 2048 FFTOFDM technology. On the other hand, Wi-Fi supports half duplex communication with 52 FFT OFDM technology.
Operating Forums
WiMAX spectrum is owned by WiMAX Spectrum Owners Alliance (WiSOA), which is responsible for regulating, commercialize and deploy the WiMAX spectrum in 2.3 to 2.5 GHz and 3.4 to 3.5 GHz ranges. The WiMAX standard is certified by WiMAX forum, which is an industry led, non-profit organization for promoting and certifying IEEE 802.16 compliant broadband wireless products.
On the contrary, Wi-Fi is certified by Wi-Fi Alliance, a global organization which certifies interoperability of IEEE 802.11 compliant wireless products and promotes the global wireless standards.
Data Rates
Wi-Fi can transmit data at the fastest, up to 54 Megabits per second, whereas speed for WiMAX can reach up to 70 Megabits per second. It currently provides 40 Megabits per second for one wireless channel for both fixed and mobile applications.WiMAX can deliver uplink speed of 25 Megabits per second (Mbps) and downlink speed of 63 Megabits per second (Mpbs). Updated version of WiMAX is expected to deliver speed up to 1 Gigabits per Second (Gbps).
Security
WiMAX uses encryption techniques like Triple Data Encryption Algorithm and Advanced Encryption Standards, whereas Wi-Fi uses Advanced Encryption Standards and RC4.
Wi-Fi provides security methods like Wireless Protected Access (WPA), Wireless Protected Access (WPA2) and Extended Extensible Authentication Protocol (EAP). However, it does not has any Quality of Service (QoS) management yet.
WiMAX uses security protocols like Privacy Key Management Protocol Version 2 (PKMP2), Extensible Authentication Protocol (EAP) and Advanced Encryption Standard (EAS). These protocols ensure Quality of Service (QoS) protection of both audio and video streaming services.
This feature allows service providers to manage the network traffic based on the subscriber agreement and charge the subscriber extra for Quality of Service (QoS) protection.
Mobility
Wi-Fi currently provides the fixed version, the mobile version being in development. On the other hand, WiMAX provides both fixed and mobile versions. The fixed version (802.16d and 802.16e) is used for residential as well as business areas, whereas the mobile version is seen to replace existing mobile network technologies like GSM or CDMA.
Also Read: Internet of Things (IOT) and Its Applications in Electrical Power Industry
Future with WiMAX
WiMAX seems to be the promising next generation wireless network platform, with high speed and large coverage area capabilities. It does not require line of sight and can efficiently bandwidth intensive applications like real time video. In simple words, using WiMAX, one can listen to music and watch videos on his/her electronic device.
WiMAX is currently expected to replace existing DSL and other cable broadband technologies like various companies are employing WIMAX to provide broadband connections.
It can also be a replacement for mobile communication technologies like GSM and CDMA. Using WiMAX, point to point connections can be created, with a transmission rate which can support multiple E1 and T1 lines.
By ensuring Quality of Service and Multicasting services, WiMAX can provide Voice over Internet Protocol (VoIP) and Internet Protocol Television (IPTV) apart from fast broadband connections. Also, large banks can use WiMAX networks for connecting branches and Automated Teller Machines (ATMs) to the same network.
So, this is a basic overview about WiMAX. This might be a new technology for beginners to learn, but the implementation has already been started, even in African countries. While WiMAX is the latest step in the area network scale, the final step would be the Global Area Network (GAN) (Proposed Standard – IEEE 802.20). Any latest updates regarding WiMAX and GAN is welcome in the comments section below.
You may also read:
- What are Industrial Communication Networks? An Overview
- Batteries Wiring Connections and Diagrams
- Lighting Design Calculation in a Building – Step by Step
The post What is WiMAX? Difference between Broadband WiMax and WiFi appeared first on Electrical Technology.
December 15, 2017 at 08:06AM by Department of EEE, ADBU: http://ift.tt/2AyIRVT
Video: Things that every Electrical Engineer should know
How Does Capacitor Bank Improve Power Factor?
Things About MCBs That Every Electrical Engineers Beginners Should Know!
How to Use a Multimeter, Basics Every Electrical Engineer Need to Know
Basic Electrical Schematic Symbols That Every Electrical Engineers Beginners Should Know
The Easiest Way to Measure Ground Resistance That Every Electricians Should Know!
Video: Home Electrical Wiring
Primary Injection Testing Of Protection System For Wiring Errors Between VTs / CTs and Relays
Credit- Electrical Engineering Portal. Published by Department of EEE, ADBU: tinyurl.com/eee-adbu
What is Automated Fingerprint Identification System and How it Works?
Automated Fingerprint Identification System – Modules & Applications
Introduction to Fingerprint Identification System
Fingerprint Identification system or Dactyloscopy is a unique process of identification by comparing the fingerprint impressions of individuals. It used the fact no two individuals have similar finger patterns. It is one of widely used techniques for acquiring details of a person and is an easy and convenient way to identify a person.
Figure 1: Types of Fingerprints
Every human finger skin has pattern of dark lines (ridges) along with white lines (valleys) between them. Points at which structure of the ridge changes is known as Minutiae. Each human finger has different ridge pattern. These patterns can be Arches (where ridges enter and exit on same sides), Loops (where ridges enter on one side and exit on another) and Whorls (circles or mixtures of different patterns)
Fingerprints can be obtained using two methods – Chemical and Automatic Identification Method
In the former, a surface is sprayed with different chemicals like Cyanoacrylate, Ninhydrin, Magnetic Powder etc. and the finger print patterns can then be lifted using a clear tape. In the latter, the fingerprint images are acquired by different sensors like Capacitive Sensors (obtain pixel value based on capacitance of the fingerprint ridges), Optical Scanners (uses prisms to detect change in reflectance of light by each ridge or valley) and Thermal Scanner (measures differences in temperature over time to create a digital image).
Digital Image Processing in Fingerprint Identification System
The basic steps for digital image processing in Fingerprint Identification involves acquiring, storing and analyzing the fingerprint data.
The first step involves acquiring fingerprint images from different sensors like – Optical or Capacitive Sensor. The charge coupled device present in the optical scanner consists of light sensitive diodes which emit electrical signals when illuminated. These tiny dots when hit a target spot form the pixels and an array of pixels form the image. Once the finger is placed on the monitor, the image is acquired by illuminating the ridges of the finger.
The second step involves storing and processing the images using the below given steps.
- Image Segmentation: It involves removal of unwanted features from the acquired image. Procedure followed is Thresholding, wherein the pixels having intensity (gray level value) greater than a particular threshold is considered, whereas those having intensity lesser than the threshold value are removed or deleted.
- Image Normalization: It involves obtaining a uniform intensity pattern for the whole image. This is done so that the image pixels are in a desired range of gray values
- Image Orientation: The image is formed by calculating the orientation at each point. The orientation is in turn determined by calculating the average of vector orthogonal to the gradient of each pixel at X and Y directions.
- Image Filtering: This involves using various techniques like Gabor or Butterworth Filters to remove unwanted noise.
- Image Binarization: This involves conversion of the filtered image to binary image using thresholding technique, to improve the contrast. It utilizes global thresholding technique, wherein pixel value greater than the threshold is set to 1 and pixel value less than the threshold is set to 0.
- Image thinning: This is done to preserve connectivity of the ridges and involves eliminating foreground pixels.
The third step involves analyzing the images, by extracting minutiae details from the processed image and then comparing these details with those of the already stored templates. This is achieved by calculating the crossing number (half of sum of differences) between pair of pixels in aneight-connected neighborhood. This gives a unique identification for each characteristic of the fingerprint.
Fingerprint modules
To achieve fingerprint identification using microcontroller, two types of fingerprint modules can be used – SM630 and R305.
Let us have a brief idea about the two.
a. R305:
Figure 2: R305 Fingerprint Scanner
It is a 4 pin, Transistor Transistor Logic (TTL) compatible module, which communicated with Microcontroller through Serial UART communication.While the TD pin connects with the RXD pin of Microcontroller, RD pin connects with the TXD pin of Microcontroller. It supports semiduplex asychronous serial communication with default baud rate of 57600bps (acceptable baud rate can be between 9600 to 115200bps).
The transferred frame is a 10 bit frame with a low level start bit, 8-bit command or data and stop bit. Once powered up, it takes about 500 miliseconds for initialization. The system resources consist of a 512 bytes memory , set as a notepad and two 512 byte character file buffer.
b. SM630:
Figure 3: SM630 Fingerprint Scanner
It is similar to R305 in terms of pin configuration and comunication technique used. Unique features include self developed fingerprint algorithm, self adaptive parameter adjustment mechanism, low cost and power consumption, easy to use and portable integrated design. It consists of 768 fingerprint templates.
Here we are going to use Sunrom’s R305 fingerprint sensor which is connected to an interface board, 1125. It consists of three buttons – ADD, EMPTY and SEARCH. Either these buttons can be used or external commands can be sent to the board from the microcontroller.
In the below circuit, we interface the fingerprint sensor board to the 8051 microcontroller, AT89S51 through serial communication. The result of the identification process is displayed on the LCD.
Once the ADD command is send from the microcontroller, the fingerprint is added to the database and the corresponding ID is sent back to the microcontroller and displayed on the LCD. In case of an error, a code (0xFF) is sent and the error message is displayed on the LCD.
Once the EMPTY command is send from the microcontroller, all the added fingerprints are deleted from the database. Response code of 0xCC indicates execution is successful, whereas response code of 0xFF indicates an error.
Once the SEARCH command is send from the microcontroller, the matched ID corresponding to the fingerprint is sent as response code from the microcontroller and the ID is displayed on the LCD. Incase of an error, response code of 0xFF is sent back.
Applications of Fingerprint Identification System
- Crime Scenes: Major application of fingerprint identification system is to identify criminals involved in any crime. One of the foremost evidence searched from the crime scenes are fingerprints on the found items. This helps in finding the criminals based on the fingerprints.
- Organizations: This technique is used to identify members of an organization based on their unique identity number. This makes sure only authorized persons can enter the secured area of the Organization and not any intruder. It also makes count of the attendance of the individual and the time spent inside the place.
- Grocery Stores: This technique is helpful in recognizing and billing an already registered user’s credit or debit card.
You may also read:
- Arduino Programming: What is Arduino and How to Program it?
- Lighting Design Calculation in a Building – Step by Step
- Fuse and Types of Fuses
The post What is Automated Fingerprint Identification System and How it Works? appeared first on Electrical Technology.
December 13, 2017 at 05:03AM by Department of EEE, ADBU: http://ift.tt/2AyIRVT
Voltage Regulation By Transformer Off-Load Tap Changer, On-Load Tap Changer and AVR
 |
| Transformer Voltage Regulation (Off-Load Tap Changer, On-Load Tap Changer and AVR) - photo credit: ABB |
Of course the same advice is valid if an on-load tap-changer is left in service but without operation for a long period.
7 Bad Effects Of Corona On Transmission Lines
Information required for design purposes is obtained mainly through experimental studies.
10 Different Duty Types (Load Cycle) Of A Three-Phase Asynchronous Motors
 |
| (photo credit: ABB) |
Protections For Medium Voltage Synchronous Machines (Generators) – IEEE C37-2 Codes
By EEE, ADBU
How Bad Harmonics Influence The Work Of Rotating Machines (Induction Motors)
By EEE, ADBU
Thumb Rule-12 (Quick Reference of DG Set)
|
Standard Size of The DG sets |
||||
| KVA | KVA | KVA | KVA | KVA |
| 7.5 KVA | 20KVA | 35 KVA | 62.5 KVA | 100 KVA |
| 10 KVA | 25 KVA | 40 KVA | 75 KVA | 125 KVA |
| 15 KVA | 30 KVA | 50 KVA | 82.5 KVA | 200 KVA |
|
D.G Foundation Bar Size |
|
| Rating of D.G set | Size of Bar |
| Up to 82.5 KVA | 10MM |
| 100 KVA To 200 KVA | 12MM |
| 250 KVA to 500KVA | 16MM |
|
Minimum Capacity of Fuel Service Tank |
|
| AS per CPWD | |
| Capacity of DG set | Minimum Fuel Tank Capacity |
| Upto 25 KVA | 100 Liters |
| Above 25 to 62.5 KVA | 120 Liters |
| Above 62.5 KVA to 125 KVA | 225 Liters |
| Above 125 KVA to 200 KVA | 285 Liters |
| Above 200 KVA to 380 KVA | 500 Liters |
| Above 380 KVA to 500 KVA | 700 Liters |
| Above 500 KVA to 750 KVA | 900 Liters |
|
Battery Size for D.G Set |
|||
|
AS per CPWD |
|||
| DG Set Capacity | Battery Capacity (AH) | Cu Cable Size (Sq. mm) | Electrical System (Volts) |
|
Up to 25 KVA |
88 | 35 |
12 |
|
Above 25 KVA upto 62.5 KVA |
120 | 50 |
12 |
|
Above 62.5 KVA up to 82.5 KVA |
150 | 50 |
12 |
|
Above 82.5.KVA up to 125 KVA |
180 | 50 |
12 |
|
Above 125 KVA up to 500 KVA |
180 | 70 |
12 |
|
Above 500 KVA |
360 | 70 |
24 |
|
Depths of PCC (Plain Cement Concrete) for DG Set |
|
|
As per CPWD |
|
| DG Set Capacity (KVA) | Typical Depth of PCC Foundation (For soil bearing capacity 5000 kg/sq meter) |
| 750-2000 | 600 mm |
| 625 | 400 mm |
| 320-500 | 400 mm |
| 200-320 | 400 mm |
| 82.5 -200 | 400 mm |
| Upto 82.5 | 200 mm |
|
Foundation & Earthing for D.G Set |
|
|
As Per CPWD |
|
| Ieam | Descriptions |
| D.G set inside Room | A PCC foundation (1:2:4, M-20 grade) of approximate depth 150 mm above the finished Generator set Room Floor level |
| The length and breadth of foundation should be at least 250 mm more on all sides than the size of the enclosure. | |
| D.G set in Open Room | A PCC (1:2:4, M-20 grade) foundation of weight 2.5 times the operating weight of the Generator set with enclosure or as recommended by the Generator set manufacturer, whichever is higher |
| 300 mm of this foundation height should be above the ground level. The length and breadth of foundation should be at least 250 mm more on all sides than the size of enclosure. | |
| Earthing | Copper plate earthing (Neutral Grounding) shall be provided for DG Sets of capacity 500 KVA or above |
| whereas G.I. plate earthing (Neutral Grounding) shall be provided for DG Sets below 500 KVA capacity. The body earthing shall generally be of G.I | |
| Numbers of earthing for each DG Sets | 2No’s earthing sets for Genset/ control panel body. |
| 2No’s earthing sets for neutral. | |
| In case there are more than one DG Set in one location, independent two nos. neutral earthing shall be provided for each DG set. However, two nos. earthing sets shall be common for the body earthing of DG Sets | |
| DG Set of 500 KVA capacity or above:- Copper strip | |
| DG Set below 500 KVA capacity:- GI strip | |
|
D.G Detail according to Size |
|||||
| D.G Size (KVA) | L x W x H (Canopy) mm | Approx Weight (Kg) | Fuel Tank (Ltrs) | Fuel Consumption (Ltr/hr) | Oil Consumption (Ltr/hr) |
| 12.5 | 2040 x 1230 x 1450 | 1050 | 60 | 2.3 | 0.02 |
| 15 | 2040 x 1230 x 1450 | 1050 | 65 | 2.3 | 0.02 |
| 20 | 2240 x 1230 x 1450 | 1300 | 65 | 3.7 | 0.03 |
| 30 | 2510 x 1130 x 1450 | 1300 | 65 | 6.3 | 0.03 |
| 40 | 3350 x 1180 x 1650 | 1500 | 100 | 7.8 | 0.03 |
| 50 | 3350 x 1180 x 1650 | 1500 | 100 | 8.3 | 0.03 |
| 62.5 | 3350 x 1180 x 1650 | 1930 | 150 | 10.5 | 0.03 |
| 75 | 3605 x 1405 x 1600 | 1950 | 150 | 13 | 0.03 |
| 100 | 3940 x 1700 x 1850 | 2500 | 300 | 15.7 | 0.05 |
| 125 | 3950 x 1700 x 1850 | 2700 | 300 | 19 | 0.05 |
| 140 | 4600 x 1850 x 1950 | 3580 | 300 | 22.6 | 0.06 |
| 160 | 4600 x 1850 x 1950 | 3720 | 450 | 25.9 | 0.14 |
| 180 | 4970 x 1730 x 2045 | 3870 | 450 | 27.7 | 0.14 |
| 200 | 4970 x 1730 x 2045 | 3950 | 450 | 29.8 | 0.14 |
| 250 | 4970 x 1730 x 2050 | 4660 | 450 | 37.7 | 0.15 |
| 275 | 5700 x 2030 x 2515 | 5860 | 450 | 50 | 0.15 |
| 320 | 5700 x 2030 x 2515 | 5860 | 450 | 57 | 0.3 |
| 400 | 5905 x 2030 x 2520 | 6180 | 990 | 65.1 | 0.3 |
| 500 | 6205 x 2030 x 2550 | 6990 | 990 | 81.3 | 0.3 |
|
FUEL CONSUMPTION FOR DG SET: |
|
| Generator KVA | Diesel consumption Liter per hour |
| 5 | 1.25 |
| 15 | 2.91 |
| 20 | 4.78 |
| 25 | 4.78 |
| 30 | 6.55 |
| 40 | 8.11 |
| 50 | 10.19 |
| 62.5 | 10.92 |
| 75 | 13.52 |
| 82.5 | 13.52 |
| 125 | 19.76 |
| 140 | 23.4 |
| 200 | 30.99 |
|
D.G Spacing Guidance |
|||
| Description | DG set with Acoustic Enclosure | Open DG set in room. | |
| in Open Area | in Closed Area | ||
| Free space on both sides | Min. 1.5 m | Min. 1.5 m | Min. 2 m |
| Free space at front side (Radiator Hot air outlet at Front) | Min. 3 m | Min. 3 m | N/A |
| Free space at front side (Radiator Hot air outlet at Top) | Min. 1.0 m | Min. 1.5 m | N/A |
| Free space at rear side (Alternator) |
Min. 2 m | Min. 2 m | Min. 2 m |
| Fresh air inlet opening area | N/A | N/A | Min 1.5 times of the Radiator area. |
| Hot air discharge opening area | N/A | N/A | Min 2.5 times of the Radiator area. |
| Distance between two sets | Min 1.5 meter between two canopies |
Min 1.5 meter between two canopies |
Min 1.5 meter between two foundations. |
December 01, 2017 at 07:03PM
Voltage Regulators Used To Control The Voltage At The End Of a Distribution Feeder
By EEE, ADBU
